LiveCompare security
Summary
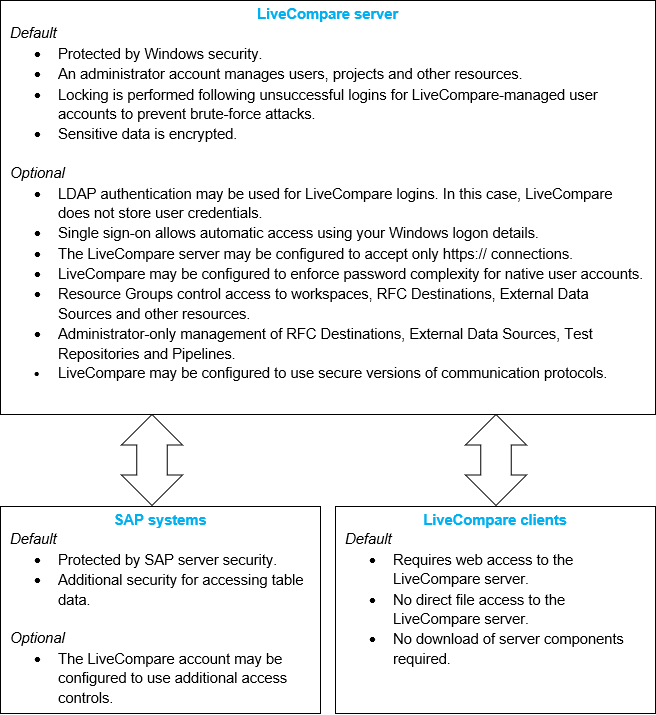
LiveCompare is installed on a Windows server machine, and accessed from one or more client machines, with SAP components provided as transports to be installed on the systems to be analyzed. Security measures are in place for each part of the installation, as shown in the following diagram.
SAP
LiveCompare accesses SAP by means of RFC Destinations which are created in the LiveCompare hierarchy. Each RFC Destination is associated with an SAP user account, which may be made a Communications Data user, so that it may not be used to sign in to SAP interactively. LiveCompare provides a set of roles which should be applied to each SAP user account as part of the installation process. The roles provide the minimal amount of access required by LiveCompare to perform its analysis tasks. The following roles are provided.
| Role | Description |
|---|---|
| /ICORP/LC_CORE_AUTHS | LiveCompare core authorizations. |
/ICORP/LC_HR_AUTHS3
|
Authorizations required for HR systems. |
/ICORP/LC_BW_AUTHS
|
Authorizations required for BW systems. |
/ICORP/LC_700_AUTHS
|
Authorizations required for 700 kernel releases and above. |
Access to LiveCompare's SAP components from SAP itself is restricted by each customer's SAP security model. For example, users of SAP at your site may be given access to only a limited set of programs and transactions, without the ability to create or modify data dictionary objects. LiveCompare's SAP components are stored in the /ICORP/ namespace, to which normal users may be given restricted access by an SAP Administrator.
LiveCompare includes an additional security feature relating to SAP table access. The function which retrieves SAP table metadata checks for the authorization object S_TABU_DIS, and if that check fails, the function checks for authorization object S_TABU_NAM. See the LiveCompare table security topic for further details.
LiveCompare includes support for a tables to ignore list for each RFC Destination. LiveCompare prevents access to the contents of tables on the ignore list.
LiveCompare retrieves and analyzes SAP data, but it is limited to read-only access.
Server
The server portion of LiveCompare is installed on a Windows server machine. Access to the LiveCompare installation is determined by a customer's Windows security model. For example, if a user doesn't have file access to the Windows server on which LiveCompare is installed, they won't be able to modify the LiveCompare installation. LiveCompare's configuration files aren’t directly accessible via the application's user interface.
LiveCompare supports single sign-on, which allows automatic access to the application using your Windows sign in details.
LiveCompare Administrator
A LiveCompare Administrator account is created when LiveCompare is installed, and one of the configuration steps described in the Installation and Configuration Guide is to secure the Administrator account by changing its password. Administrators are the only type of user able to create or delete user accounts, or create, delete or modify Resource Groups. Additionally, LiveCompare may be configured so that only Administrators may do the following:
-
Create, delete or modify RFC Destinations.
-
Create, delete or modify External Data Sources.
-
Create, delete or modify Test Repositories.
-
Create, delete or modify Pipelines.
Users
LiveCompare's user accounts may be imported from an LDAP server by a LiveCompare Administrator. In this case, users sign in to LiveCompare using their Windows username and password, and LiveCompare doesn't store their password details. If a user's LDAP account in Windows is removed or disabled, they won't be able to sign in to LiveCompare.
An LDAP user account may be locked after a certain number of consecutive failed sign ins, if this has been configured by your Windows System Administrator. Native LiveCompare user accounts are locked after three consecutive unsuccessful sign in attempts, and must be unlocked by a LiveCompare Administrator before users are able to sign in.
Roles
An Administrator may assign each LiveCompare user to one of the following roles:
LiveCompare Editor
LiveCompare Editors may create workspaces and create, modify and run workflows. They may also access the consumer interface to run apps and view their results. LiveCompare Editors may also create, modify and delete RFC Destinations, External Data Sources and Quality Center projects if this has been allowed during the installation of LiveCompare, or afterwards by a LiveCompare Administrator.
LiveCompare Consumer
LiveCompare Consumers can run Apps and view their results. However, they aren’t able to create, view, edit or run workflows. As LiveCompare consumers to not have access to the LiveCompare hierarchy, they may not create or view the details for RFC Destinations, Quality Center Projects, S3 Buckets, External Data Sources, Vaults or Java Files.
Administrator
The Administrator role is designed for users who control user access and workspace availability. An Administrator may add or delete user accounts, assign roles to users, and manage passwords RFC Destinations and External Data Sources. Administrators can create, register and delete workspaces, and manage projects to determine which workspaces and RFC Destinations are available to which users. However, they aren’t able to run Apps or workflows, or view App or workflow results.
Partial Administrator
Only one user with LiveCompare Administrator permissions may be signed in to LiveCompare at the same time. If a second user with LiveCompare Administrator permissions signs in, they are given the Partial Administrator role, allowing them to sign out the first Administrator.
Resource Groups
Resource Groups may be set up by a LiveCompare Administrator to restrict a user's access to workspaces, RFC Destinations, External Data Sources, Pipelines, Test Repositories, ServiceNows and LUXes. If Resource Groups have been defined in LiveCompare, a Resource Group selection list box is displayed in the top right-hand corner of the studio and apps user interface screens. Users are only able to access the resources in Resource Groups of which they are a member. If a user is not a member of any Resource Groups, they won't be able to sign in to LiveCompare.
Passwords
User accounts managed by LiveCompare are protected by a one-way password scheme called PMKDF2 with added salt.
Passwords that must be decrypted (for example the password used in an RFC Destination to open a connection to SAP) are protected using the built-in Windows cryptography library. Specifically we use this provider coupled with this provider type and the CALG_RC4 algorithm.
Strong passwords
The requirement for strong passwords may be set during the installation of LiveCompare, or afterwards by a LiveCompare Administrator. A password must satisfy all the following criteria to be considered strong:
-
At least 8 characters.
-
At least 1 uppercase character.
-
At least 1 lowercase character.
-
At least 1 number.
-
At least 1 special character from this list: ` ¬ ¦ ! " £ $ € ^ & * ( ) - = + [ ] { } ; : ' @ # ~ \ | < > , . / ? <space>
An Administrator may require users to change their passwords when they next sign in. If the requirement for strong passwords has been set by an Administrator, new passwords must satisfy the strong password criteria.
The requirement for strong passwords applies to native accounts only, and not to the passwords for user accounts imported from an LDAP server.
Secure RFC connections
LiveCompare may be configured to connect to SAP using Secure Network Connections (SNC). See the Create secure RFC Destinations topic for details.
Secure FTP connections
Read Large SAP Table actions support secure FTP connections using FTP over SSL. The secure connection details are configured for an RFC Destination in its FTP tab.