Key vault secrets
To use confidential data with Tosca, you can integrate a key vault provider. This allows you to fetch secrets from a key vault which you can use for your tests, such as passwords, tokens, or sensitive information. When you do so, Tosca uses the fetched value only for a short period of time, without storing it.
It offers the following advantages:
-
Improved secret management, as you don't need to update sensitive information in Tosca anymore.
-
Improved security, as Tosca only stores the path to the secret key.
-
Improved data protection, as sensitive information is excluded from logs or test results.
To see a list of supported key vaults, see chapter "System requirements".
Limitations
The following limitations apply when using a key vault with Tosca:
-
You can't add, update, or manipulate any secrets in your key vault with Tosca.
-
You can only fetch secrets with ActionMode Input or ActionMode Insert and DataType Secret.
Fetch secrets
To fetch secrets from a key vault, you must first prepare your system under test:
-
Set up the key vault on the machine where you run your tests.
-
Stay signed in to your key vault at all times during test execution.
After preparing the SUT, use the dynamic expression {SECRET} and the following syntax:
|
Syntax: |
{SECRET[<KeyVault>][<SecretPath>][<FieldName>][<CyberArkAppId>]} |
KeyVault
The parameter KeyVault specifies the vendor of your key vault, such as HashiCorp or CyberArk. This parameter is optional for HashiCorp.
SecretPath
The parameter SecretPath specifies the path to the secret inside the key vault.
FieldName
The parameter FieldName specifies which field from the secret to fetch.
CyberArkAppId
The parameter CyberArkAppId specifies the CyberArk application ID, so use it only when your key vault is CyberArk.

|
In this example, you fetch the field DBPassword, which is located at kv/database/production/pw. To do so, you use the following syntax: {SECRET[hashicorp][kv/database/production/pw][DBPassword]} |
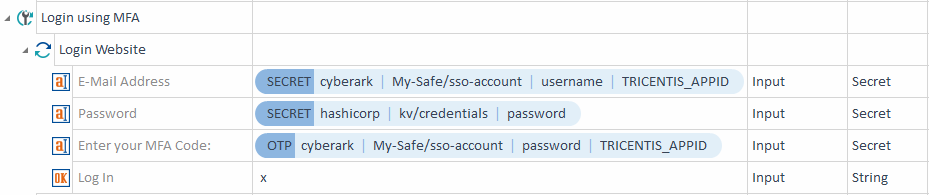
Steer MFA/SSO
You can steer MFA/SSO by generating one-time passwords. First, make sure to Fetch secrets of the system under test and store them in the secret of the key vault.
To generate a one-time password, use the dynamic expression {OTP} and the following syntax:
|
Syntax: |
{OTP[KeyVault][<SecretPath>][<FieldName>][<CyberArkAppId>]} |
The parameters match those described above in the syntax for fetching secrets.

|
In this example, you perform the following actions:
Steering MFA by generating one-time passwords |
Additional configurations
Specify a different timeout value
By default, Tosca waits 5 seconds for the key vault response before a request fails. If the default value isn't sufficient, you can specify a different timeout value.
To do so, create a test configuration parameter (TCP) named KeyVaultCommandTimeout and specify the new timeout value in milliseconds.
Specify a different path to the key vault executable
In some cases, Tosca can't find the path to your local key vault. If this happens, you need to manually specify the path.
To do so, create a TCP named KeyVaultPath and specify the path to the key vault executable:
-
For Hashicorp, enter the full path to the executable file. Be sure to include the file name in the path.
-
For CyberArk, enter the directory path to the folder that contains NetStandardPasswordSDK.dll.