Record an HTTPS application
When recording a scenario, NeoLoad acts as a go-between with the browser and the web server. With a secure connection, NeoLoad has to decipher the traffic flowing between the two entities in order to analyze its content. Each time a communication is sent, NeoLoad decodes the incoming data, analyzes it, and re-ciphers it before sending it out again. This process requires the use of certificates.
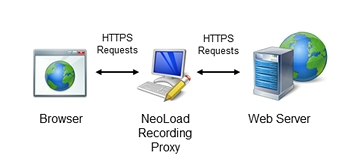
Before recording the scenario, it is recommended to close all HTTP client applications (other Web sessions, Twitter client, and so on). NeoLoad records all the HTTP flows going through the machine. It is necessary to close HTTP clients or define exclusion rules in NeoLoad to avoid unwanted requests in the recording.
Certificates
For each request using the HTTPS protocol, NeoLoad retrieves the certificate provided by the SSL server. This certificate is essential to ensure secure communication between the proxy and server. Moreover, NeoLoad takes on the role of the server, issuing a certificate that is sent to the browser to secure communication between proxy and client. This certificate, created on-the-fly by NeoLoad during recording, is not recognized by the browser as being valid, since it is not authenticated by any certificate authority. The browser displays messages warning that the certificate provided by the server (in this case NeoLoad) cannot be trusted and that, consequently, the connection cannot be secured.
Importing the authority certificate (root certificate) into NeoLoad enables each certificate generated automatically during recording to be authenticated, thus preventing the display of certificate error messages in the browser. The root certificate is placed in the certificate authorities keystore. The section Install the root certificate details the procedure to follow. Be warned that installing a root certificate in a browser creates a serious security loophole. It is important to have read and fully understood the associated risks for the machine security as set out in Security warning before proceeding.
Certificates used for SSL interception
To capture HTTPS traffic, we implement man-in-the-middle interception. You can either use our self-signed certificate named "Embedded NeoLoad Certificate" or browse to your own that you can add in the HTTP recorder panel in the Edit > Preferences > General Settings of NeoLoad.
The root certificate is created when NeoLoad is first launched and is named NeoLoad_Root_CA.cer. It can be found in the configuration sub-directory of the user profile directory.
In Windows, the configuration directory is accessible from %appdata%, for example:
C:\Users\<username>\AppData\Roaming\Neotys\NeoLoad\v8.2\conf
In Unix/Linux/Mac, the configuration directory is accessible from <$HOME>, for example:
/home/<username>/.neotys/NeoLoad/v8.2/conf/
Security warning
To decipher HTTPS requests without triggering certificate errors, a root certificate must be placed in the browser certificate authority keystore. Importing this certificate causes the browser to unquestioningly accept any certificate that is authenticated by NeoLoad (NeoLoad_Root_CA.cer) certificate. Consequently, any entity other than NeoLoad also could have its own certificates authenticated by the root certificate installed in the browser and use it unwisely. It is essential, therefore, to fully understand the dangers of installing such a certificate in a browser. You strongly recommend that this procedure only be carried out on a machine that is solely dedicated to load testing your applications.
The random generation of a higher-authority certificate means each copy of NeoLoad has its own root certificate, thus increasing system security.
You may delete a root certificate from the browser keystore as described in Remove a root certificate
New versions of NeoLoad
The NeoLoad root certificate applies to all NeoLoad versions installed on the same machine. Once the certificate is imported into the browser, it is irrelevant to import other certificates after installing a new version of NeoLoad.
Applications using client certificates
To design a scenario for an application that uses client certificates, the certificates need to be installed in NeoLoad before starting the recording. The certificates must be installed in the project preferences. For more information, see Certificate Manager
Java applets
For HTTPS requests issued by a Java applet to be correctly captured by NeoLoad, the browser Java plug-in needs to be configured to use NeoLoad recording proxy as a proxy server.
To configure the Java plug-in, follow these steps:
-
In Windows, select Java in the Control Panel.
-
Select the General tab, and click Network settings.
-
Select Use proxy server and set
localhostas the address and the NeoLoad proxy port (8090 by default) as the port. -
Click OK, and re-start your browser before making a new recording.
Start recording an HTTPS application
A secured application can be recorded:
-
in tunnel mode, as described in Start recording in tunnel mode.